The ASD Top Four, if you haven't heard of them, have become a part of the highly popularised Essential Eight.
They consist of:
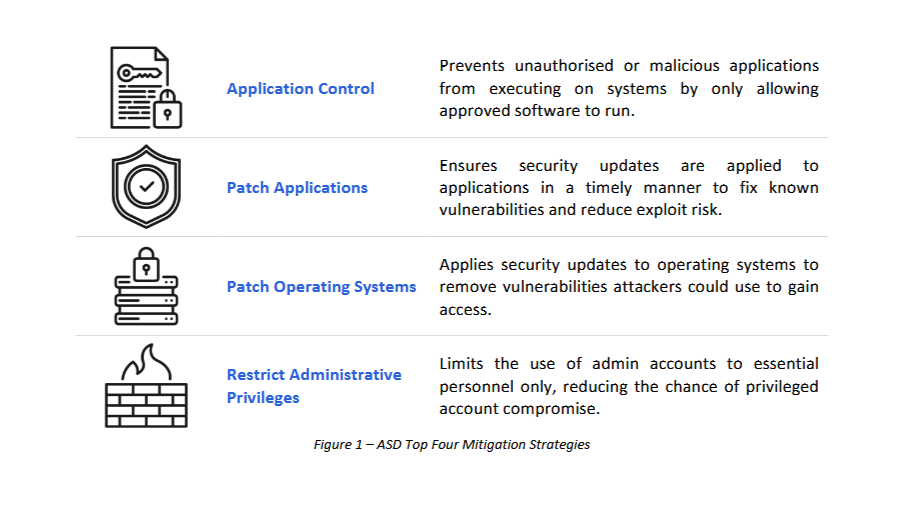
Back in the days of 2015, the ACSC produced a threat report, and while there were enough buzz words for a game of bingo, it also included a handy statistic.
Which is the Top Four were able to prevent and mitigate at least 85% of targeted cybercrime intrusions responded to by the ASD.
But how do they fare now?
Well… Obviously they are still great because they are in the current recommendation from the ASD.
Yet, more importantly, can they still boast their 85% cyber intrusion prevention rate in today's world?
I'll wager the answer is no.
That's not to discredit the four mitigation strategies.
More to say that they are an exceptional start to a cyber security strategy, and with some minor additions, you could find yourself sleeping better at night.
When thinking about including real-world evidence in this article, the internet provided me with a helpful dose of analysis paralysis up until reading a rather unfortunate incident over in Canada.
Why it's worth the investment
You may have caught the headlines "Cyber insurer denies $18 million claim" which makes you wonder what heinous crime this organisation did to have their claim rejected.
They didn't have MFA…
One article reads.
The Canadian city of Hamilton, Ontario fell victim to a ransomware attack in February 2024. This attack was similar to countless others where initial access was gained via an externally-facing machine with weak credentials, which then lead to internal infrastructure being encrypted and a ransom for the decryption binaries being posted.
And to take an excerpt out of the Australian parliament's cyber security compliance report from 2017.
The ASD says "implementing the 'Essential Eight' mitigation strategies can save organisations considerable time, money, effort and reputational damage compared to cleaning up after a compromise". ASD is also of the view that the Essential Eight are so effective it "considers them to be the cyber security baseline for all organisations".

Which seems ever more apparent with that article and the many others like it.
And helps to reinforce why the Essential Eight is so highly regarded.
So, what are the additions?
To circle back to the Top Four and their effectiveness in today's age of cloud everywhere.
Whether it's identity management, SaaS applications or your email solution.
They aren't protected and the data they hold isn't protected by the Top Four.
And without the obvious inclusion of "just add one of the Essential Eight controls", it seemed fitting to highlight business email compromise.
The ASD provide some quality guidance about how to protect against business email compromise.
In that they cover:
- Phishing and awareness training
- Multi-factor Authentication
- Strong passphrases
Not so groundbreaking but they would have changed the headlines from that article.
Two of them are easy enough to figure out alone, but phishing and awareness training is generally overlooked.
It's either the products are too expensive or that the material is dated and throws references of the Bank of America at you.
However, if you were interested, there's an awesome Australian team doing it right over at Phriendly Phishing.
From the Top Four to the Complementary Five and a bit
Without taking away from the Essential Eight, it's just plain truth when faced with the implementation costs of the full suite of the eight controls that it won't happen.
And it shouldn't feel like you're trying to boil the ocean when considering where to start on your cyber security journey.
Small steps towards to the Essential Eight will always pay dividends or $18 million dollars to be exact.
