Revisiting the Commonwealth's Cyber Posture
In preparation for the next iteration of the Commonwealth's cyber security posture report, we revisited last year's findings and refreshed ourselves on what the Australian Government has been up to.
The report's statistics are based on the coverage of cyber security goals across Australian Government entities, which comprise three groups:
- Non-corporate Commonwealth entities
- Corporate Commonwealth entities
- Commonwealth companies
Which on the surface doesn't ring any bells, but a quick search shows that there is a handy chart that lists out all the different entities with a rather random looking symbol choice for the key.
Most of which it's likely you've never heard of but to make them more tangible, I've included a couple of examples.
- The ATO or Australian Tax Office is a Non-corporate Commonwealth entity
- The Reserve Bank of Australia is a Corporate Commonwealth entity
- NBN Co Limited is a Commonwealth company
Of note, the delineation between the three types of entities are:
- Non-corporate Commonwealth entity: not a body corporate
- Corporate Commonwealth entity: a body corporate
- Commonwealth company: Corporations Act 2001 company controlled by the Commonwealth
Where a body corporate turns out to be.
A legal entity, other than a body politic or a natural person. It includes a statutory corporation, a company and an incorporated association.
And a full list of all the entities can be found here.
Now, that's a fair bit of context.
But it's worth building an understanding of what the data is based on to grasp why the statistics are what they are.
Where the Metrics Come From
The bulk of the report goes into detail about different segments of cyber security hardening which is brought up by another lengthy document labelled the Protective Security Policy Framework (PSPF).
Which essentially covers what Australian government entities should do.
For this article we'll be looking at the previously available PSPF of 22-23 as it is what was used at the time of writing for the Commonwealth report.
From the PSPF there are a couple of references in relation to cyber security, namely, policy 10 and 11.
Which translate to "Implement the Essential Eight" and "Have a look at the broader ISM".
And without wanting to write a blog that would take a week to write, lets focus in on the statistics surrounding the Essential Eight.
Essential Eight Maturity at a Glance
A quick glance may make it seem like the Commonwealth entities went backwards and forgot they needed to maintain the controls year over year.
However, over the period from the previous years audit and the most recent one.
The Essential Eight controls shuffled and changed quite dramatically, making maturity level two harder to achieve.
And in doing so, has made it harder to make a comparison.
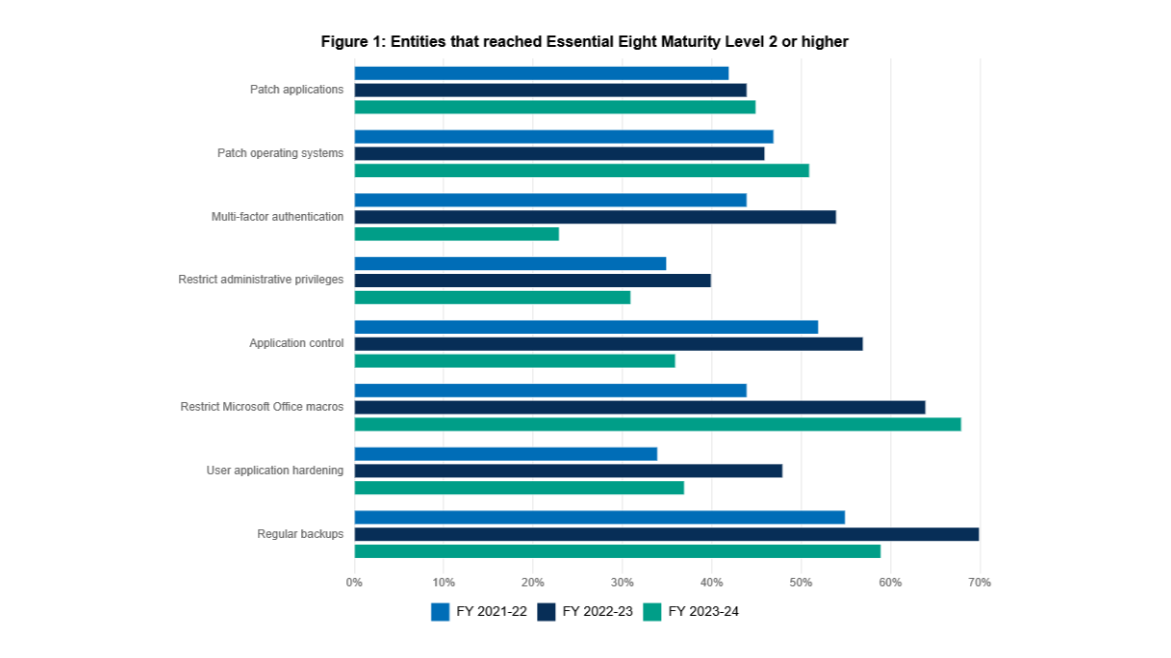
You could say that the controls that became harder to achieve were:
- Multi-factor Authentication
- Restrict Administrative Privileges
- Application Control
- User Application Hardening
- Regular Backups
Which is obviously more than half of the eight.
And having a look at the changes made between that time it's easy to see they dialled up the baseline security.
Let's dive into what the changes were and why they seemed to alter the data.
Multi-factor Authentication
A standout change is the shift away from weaker MFA toward phishing-resistant MFA for both online and local systems.
Which can be a tedious process to roll out for most organisations.
There is a common occurrence we see where Passkeys like YubiKeys will be brought out and somehow the old unsecure MFA methods still exist.
As a backup?
And a tribute to Person of Interest…

Restrict Administrative Privileges
A little bit of governance with a minor headache.
Not exactly a glowing review of the changes, but it makes it clearer why entities that were compliant before are no longer so.
Namely, Privileged accounts explicitly authorised to access online services are strictly limited to only what is required for users and services to undertake their duties.
It's obvious why it should be a control based on the principal of least privilege.
But the implementation of it can prove to be an annoyance for a maturity level one control.
The final update to the maturity level two control set is for additional management of break glass account to be tacked on to the local administrator and service accounts.
Application Control
The only changes from the past years results are for an annual validation of the rulesets and the addition of the Microsoft's recommended application blocklist.
Depending on how the application control software was setup it can change how you view these updates, you either:
- Created a software inventory and approved based on that or;
- Chose to allow any applications that ran within a period to be allowed
One of which would make life simple.
And you guessed it, creating a software inventory.
Of which if you already have a tool like Airlock, it makes the whole process easy and efficient.
You don't really need to know what the Microsoft's recommended blocklist is when there is a checkbox in the application for it.
User Application Hardening
An auditors' favourite.
Life could be simple or complicated.
Do they allow all browsers or figured out you only need to pick one.
Which is where the updates come in.
As each major browser vendor that the ASD considered for the Essential Eight has their own ideas for hardening, the ASD wanted to ensure that at least you abide by their level of strictness.
When implementing the hardening you now have to consult both and understand which is stricter than move ahead with that variant when a conflict arises.
And there's no real easy way to know what DefaultFileSystemReadGuardSetting is going to do when it comes to the user experience.
And even from Google Chrome's docs, I'm still squinting at the screen trying to figure out what the setting does.
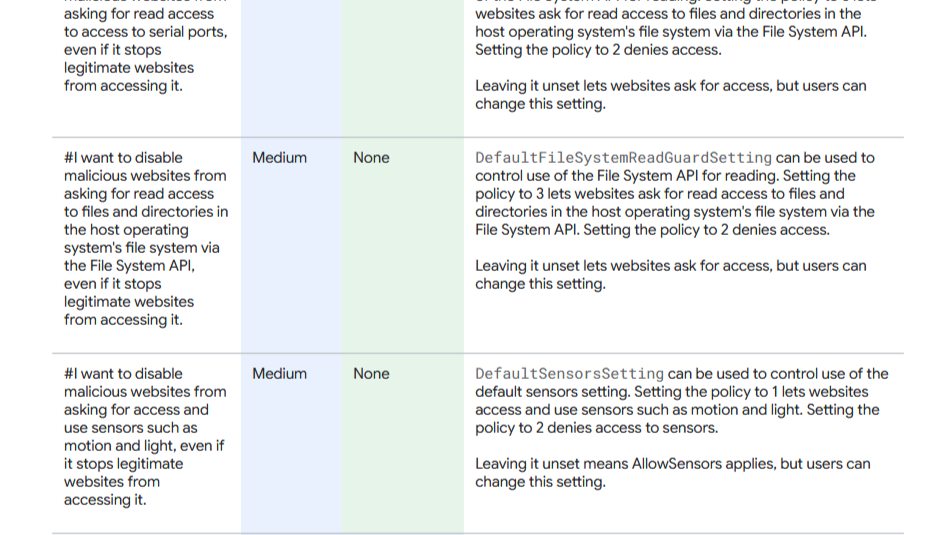
A bit of extra effort but doesn't compare to the research of all the weird and wonderful settings under the hood if you're asked to write emails to inform users about all the functionality changes they will be experiencing.
And lastly.
Regular Backups
Slipped 11% from previous years with the single addition for the need of backups to align with business criticality and business continuity requirements.
Now that doesn't directly say if those entities don't have a continuity plan period or if the backups are difficult to align to it.
Looking Ahead
We'll have to wait until November to see how Australian entities are tracking.
Fingers crossed they find themselves all moving in the positive direction.
