Removing the Nuisance of TLS Vulnerabilities from Your Vulnerability Scans
They aren't the hero of a vulnerability scan, yet they can still make it into a penetration test report.
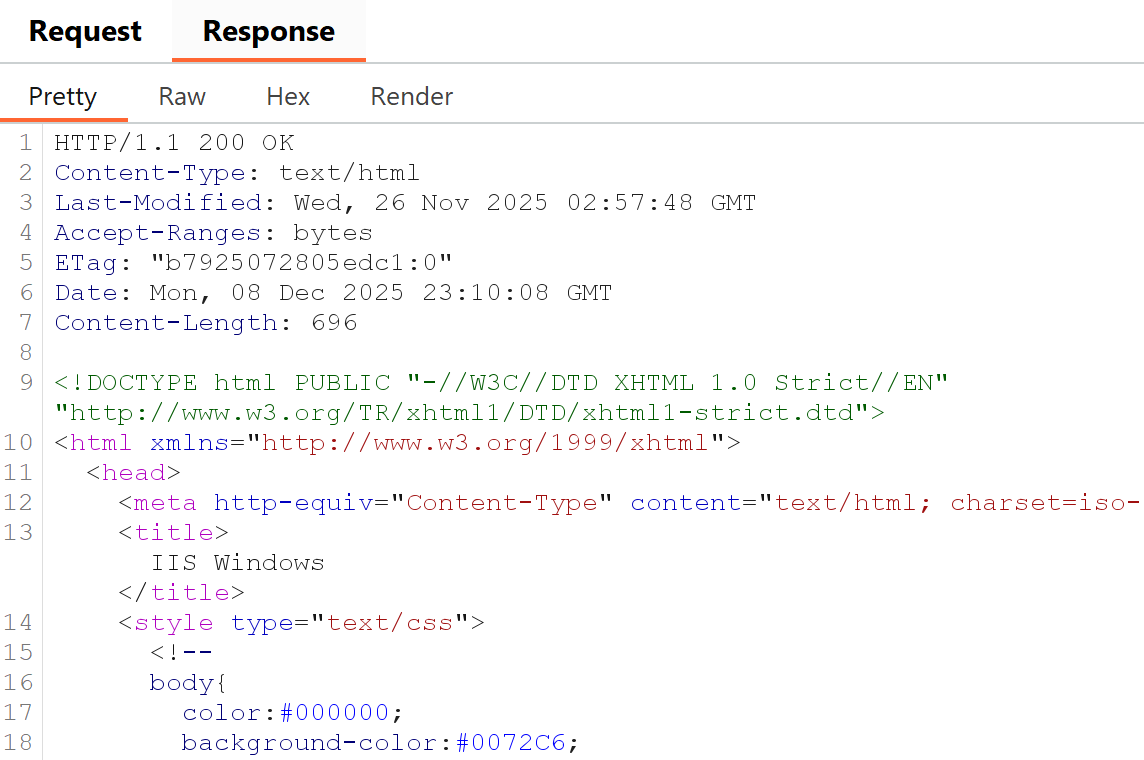
Server headers and additional information returned from a webserver can be seen in response headers.
In most cases they wont lead to your server being hacked, especially if you consistently update your software.
Yet in special cases, they can give enough information to a malicious keyboard warrior to indicate that your webserver is running an old and vulnerable version.
If it's anything like the webserver vulnerabilities of late, then you may be in for a bit of unwanted overtime.
Let's have a look at Windows IIS and an example of what is returned from the server and how to fix it.
Windows IIS
Spinning up a quick webserver we can see that the header Server: Microsoft-IIS/10.0 is returned when viewing the website.
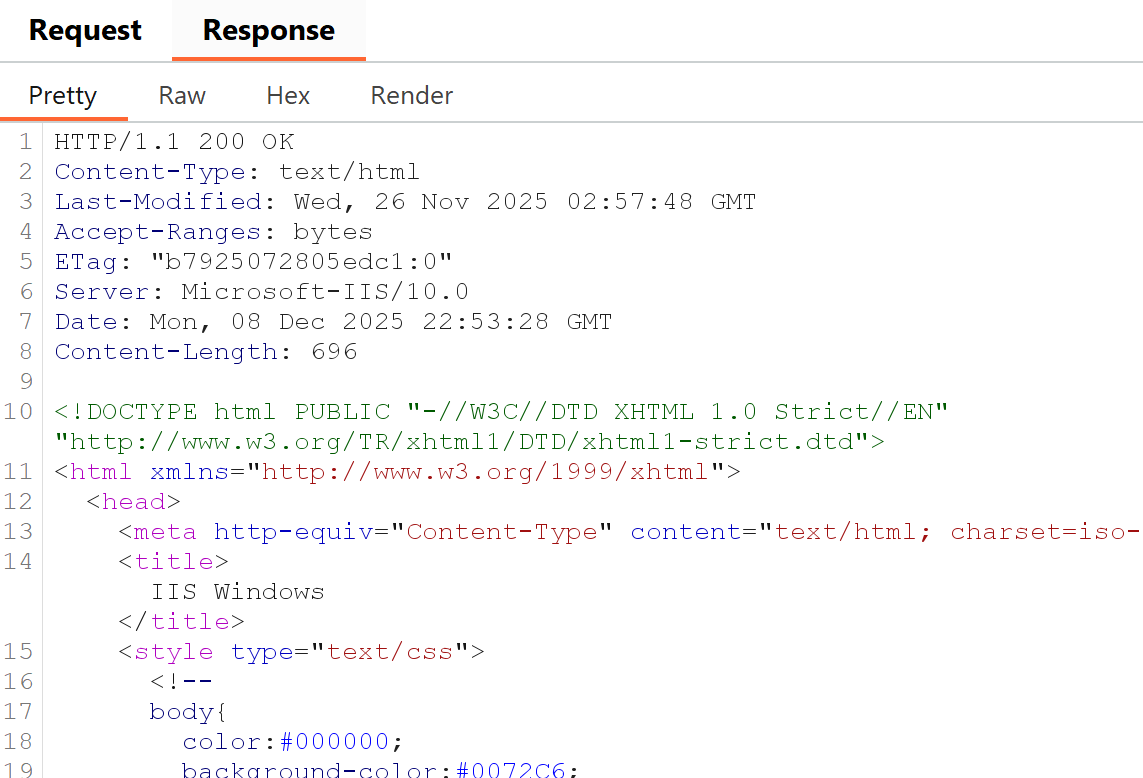
This is just one of the many headers that is attached to IIS servers, others will include:
- X-Powered-By
- X-AspNet-Version
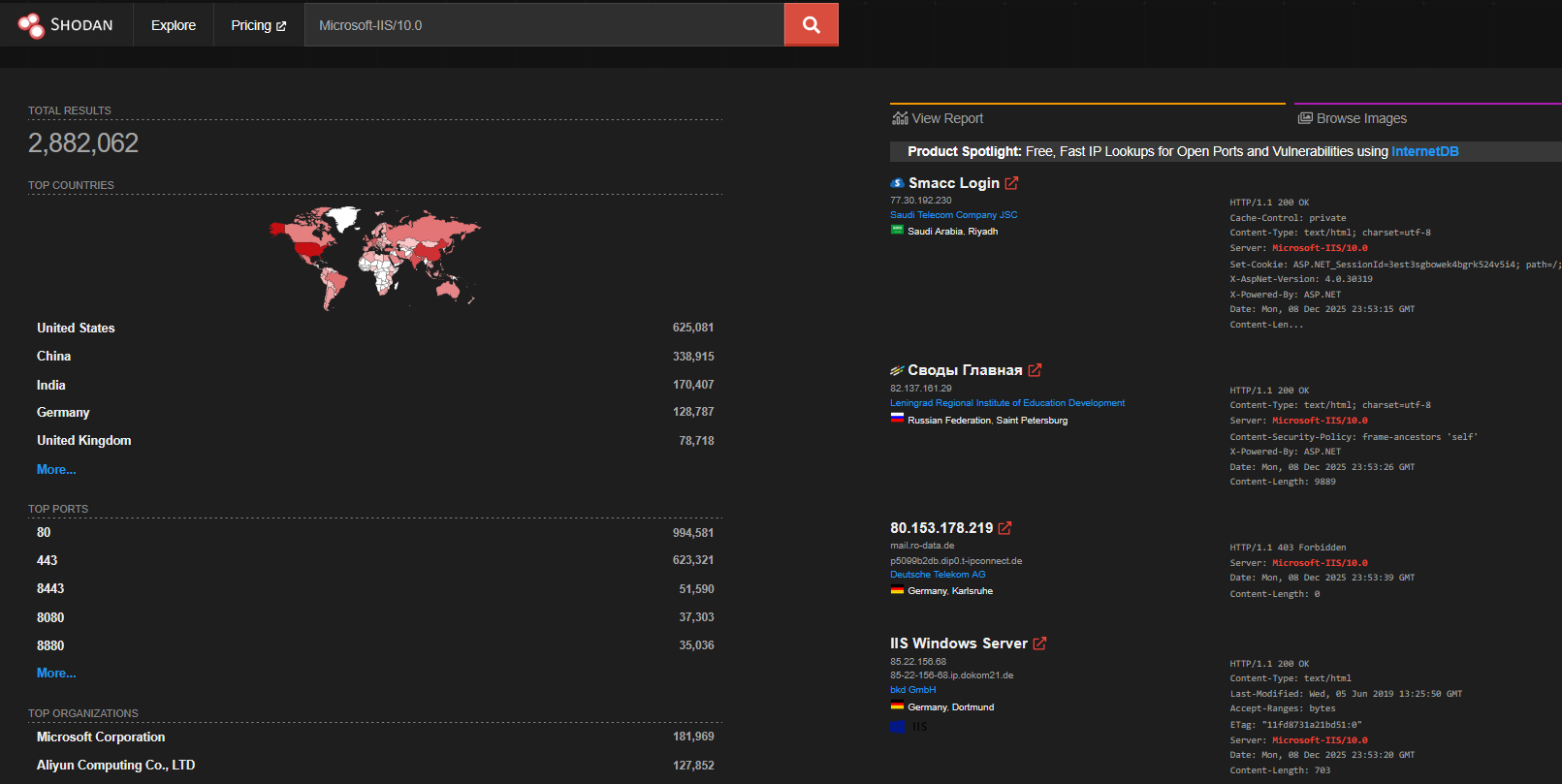
Now at this time IIS version 10.0 is secure.
Using a handy tool called Shodan, you can see a host of servers on the internet that share the same version.
Yet there was also a time when IIS version 6.0 was seen as secure and now it finds itself with a litany of vulnerabilities.
However, they still exist on the internet, and Shodan seems to have listed most of them as honeypots.
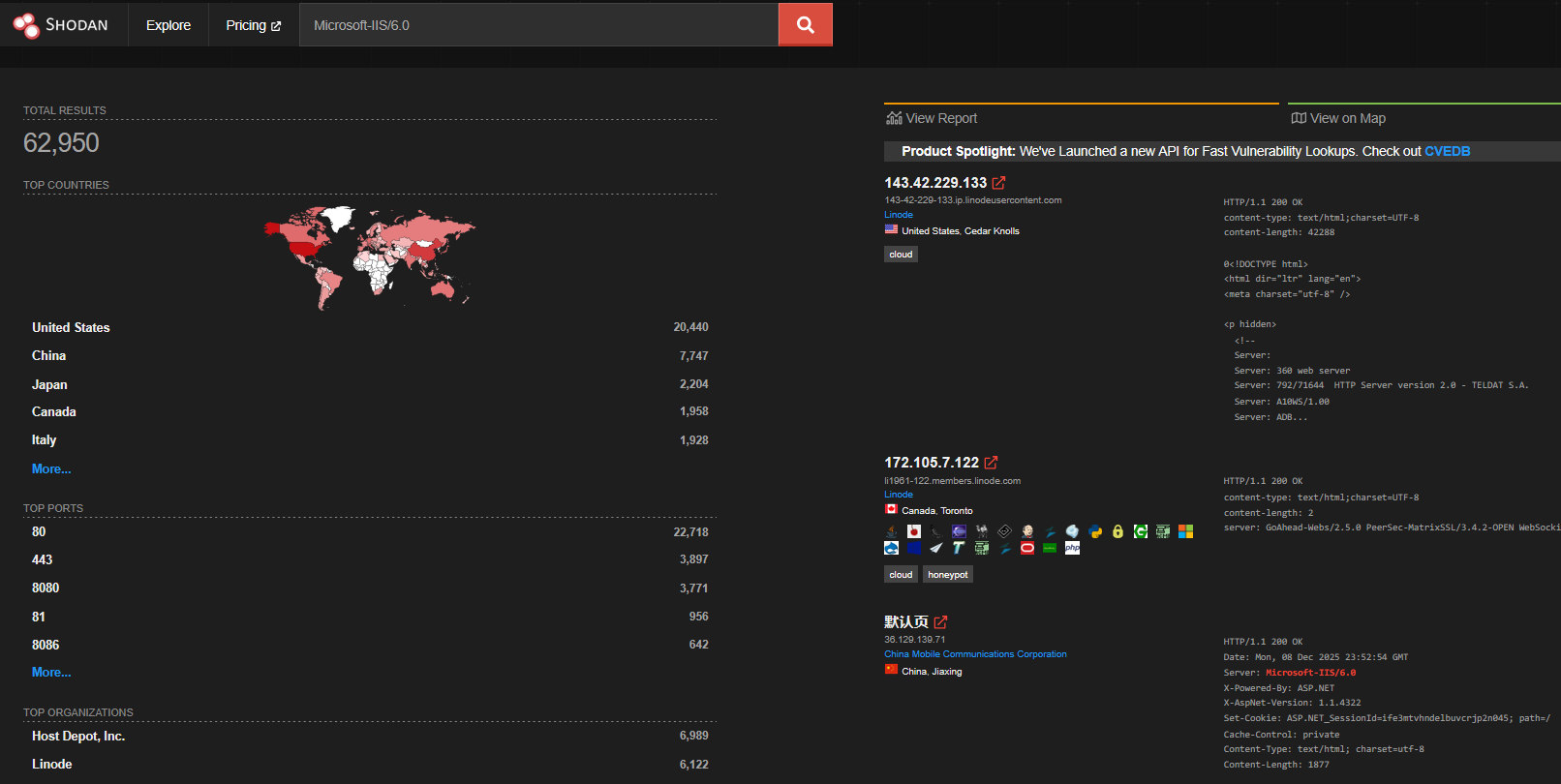
So it's fair to say that right now, it's not a massive issue but down the line it may be.
To remove the headers from the responses, open up the IIS manager and find the website in question.
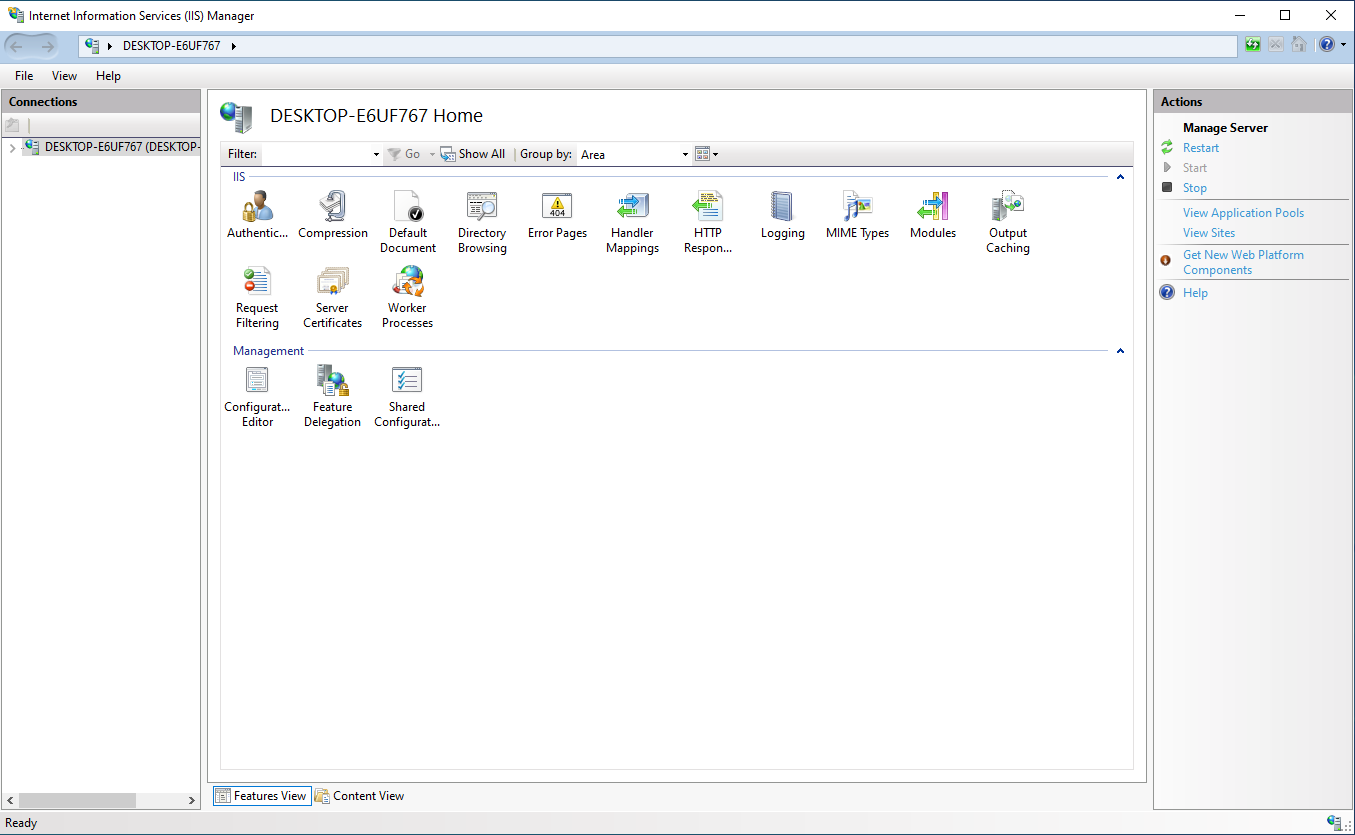
On the left window there will be the hostname of the server and the websites hosted under the Sites folder.
Navigate to the site that is showing the server header and open it up.
Once done, double click on the Configuration Editor to access the server variables.
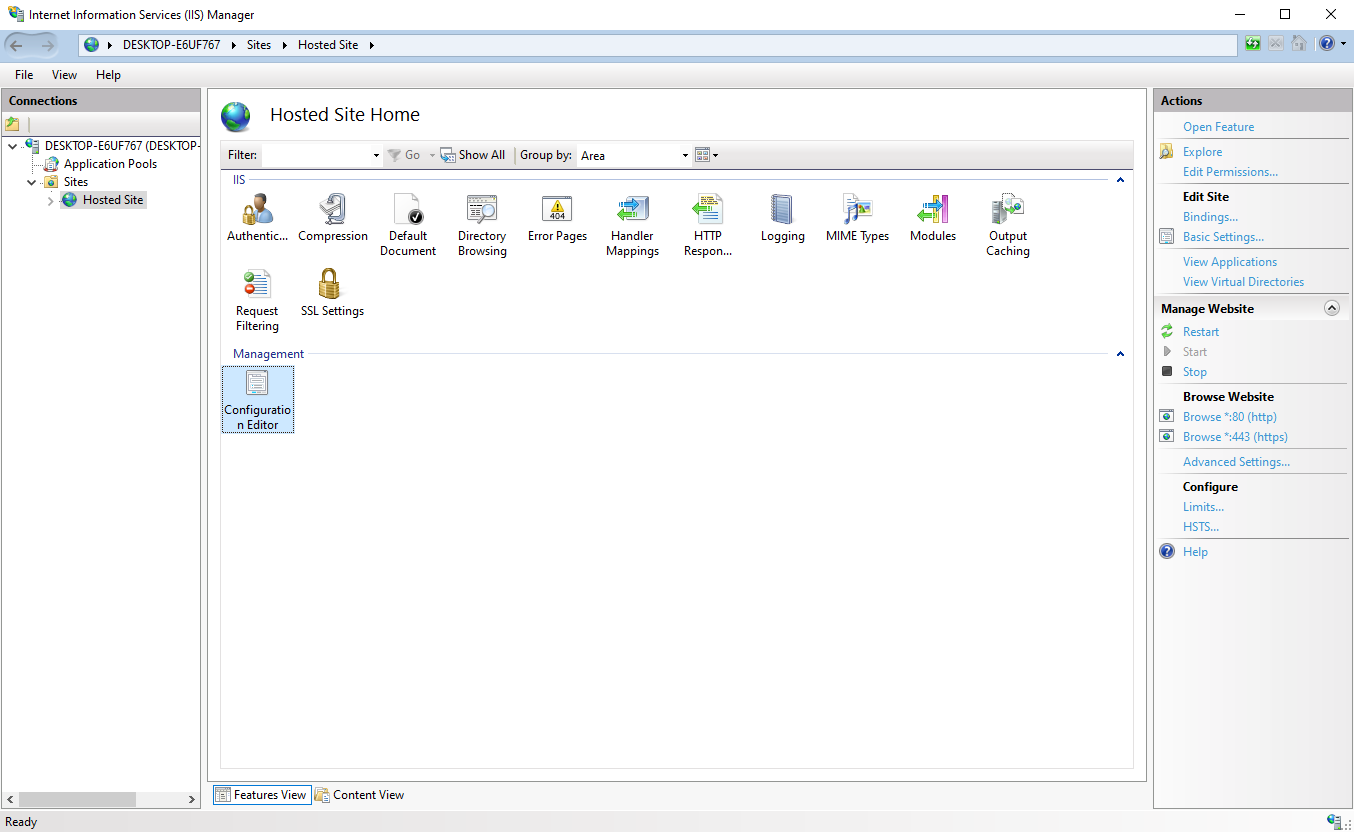
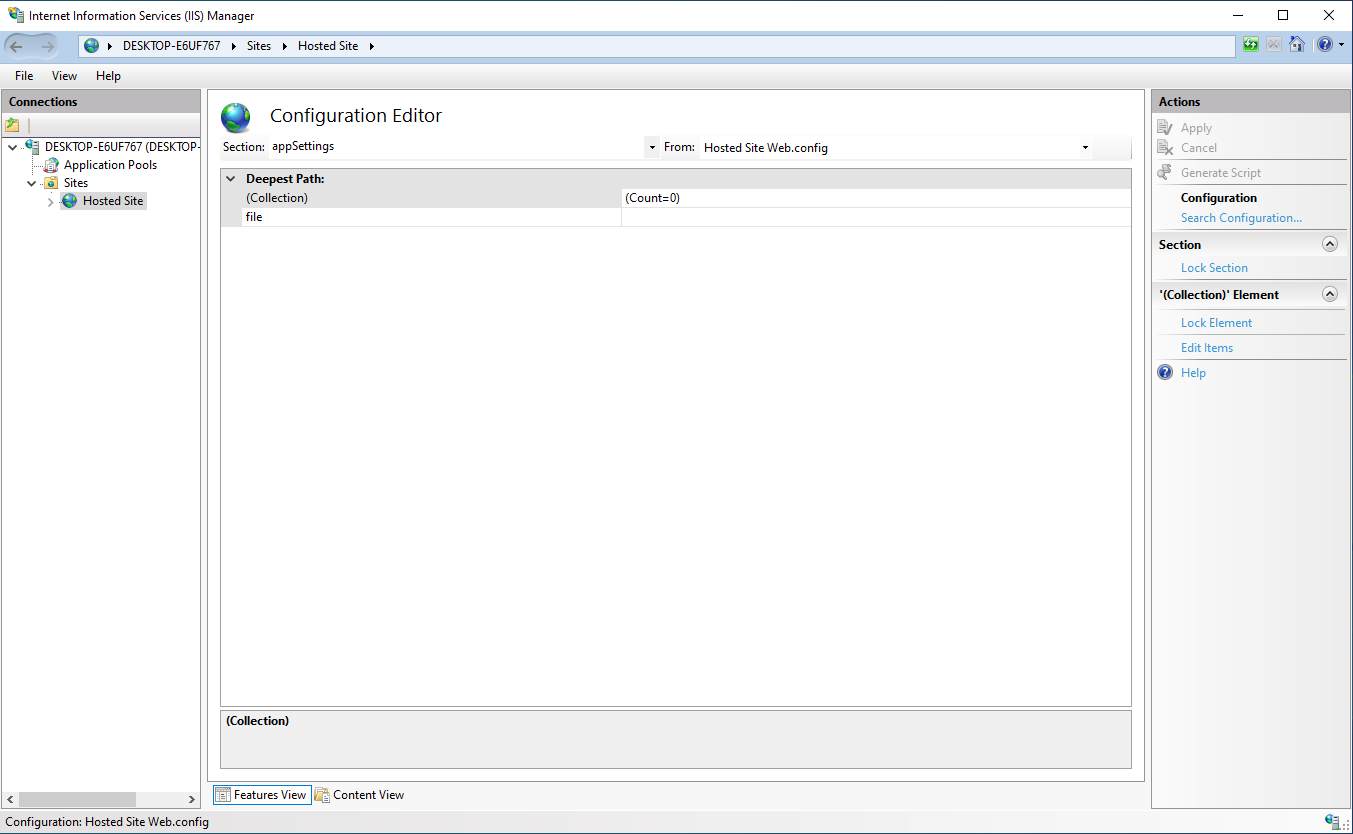
In the top drop down menu named Section, select the appSettings menu.
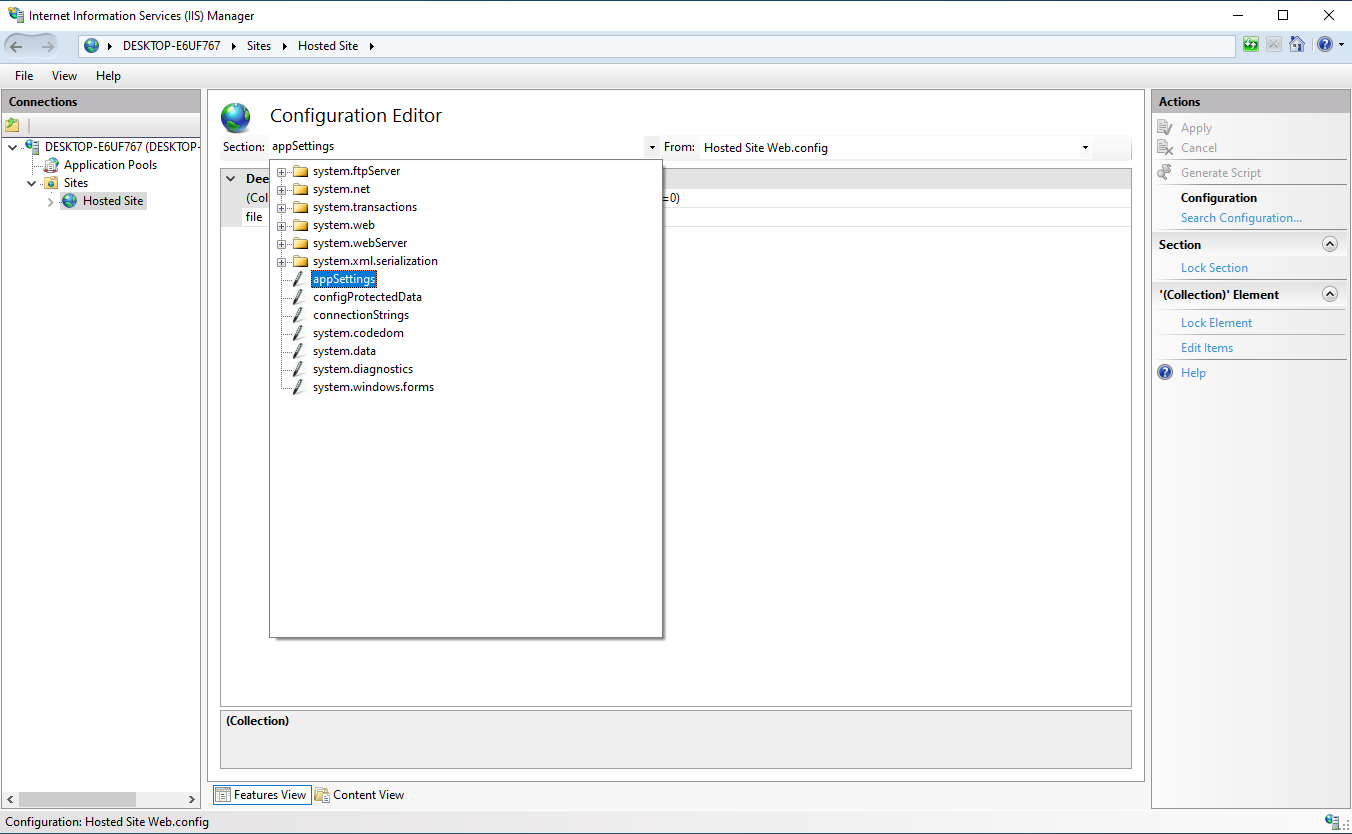
Find the variable named enableVersionHeader and it will be listed as True.
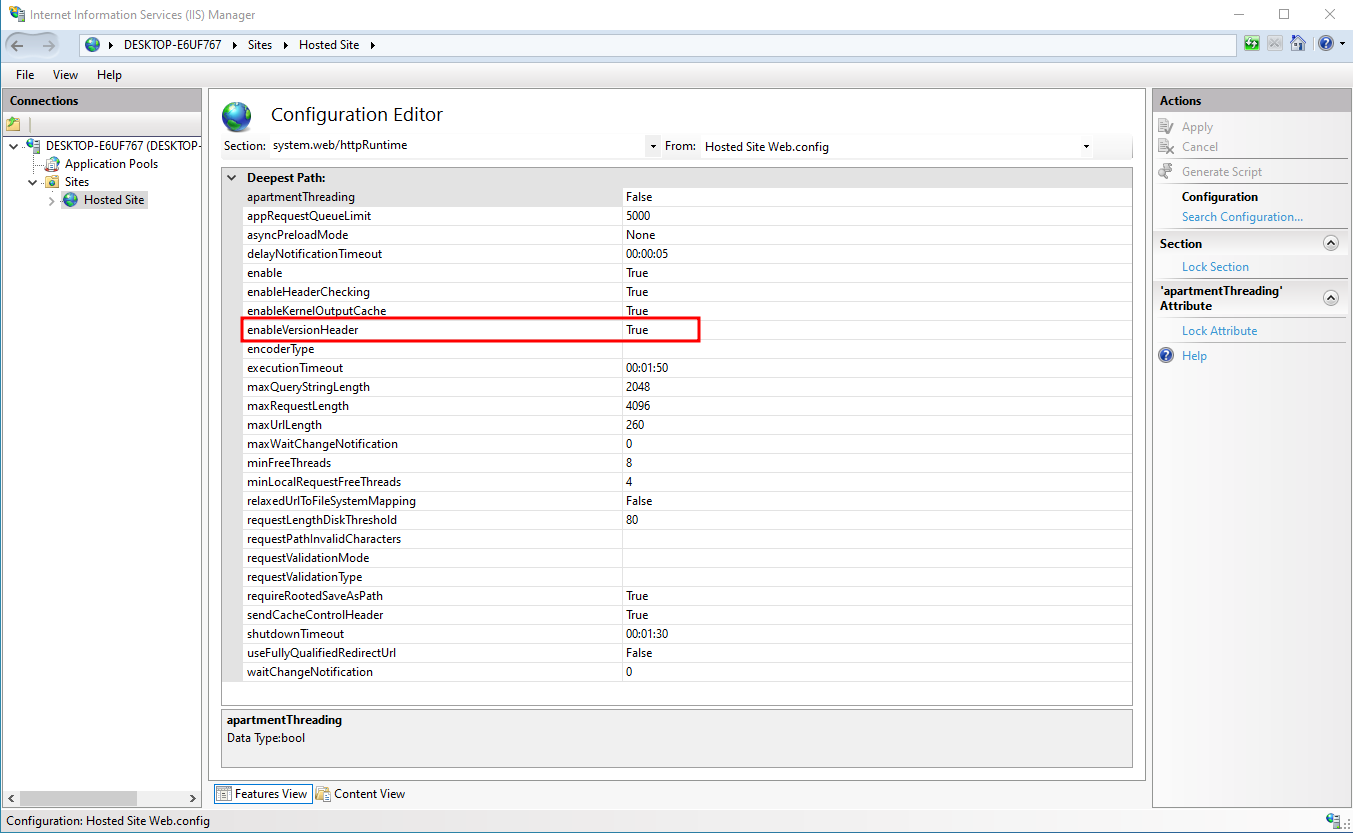
We are going to set is as False to remove any version headers.
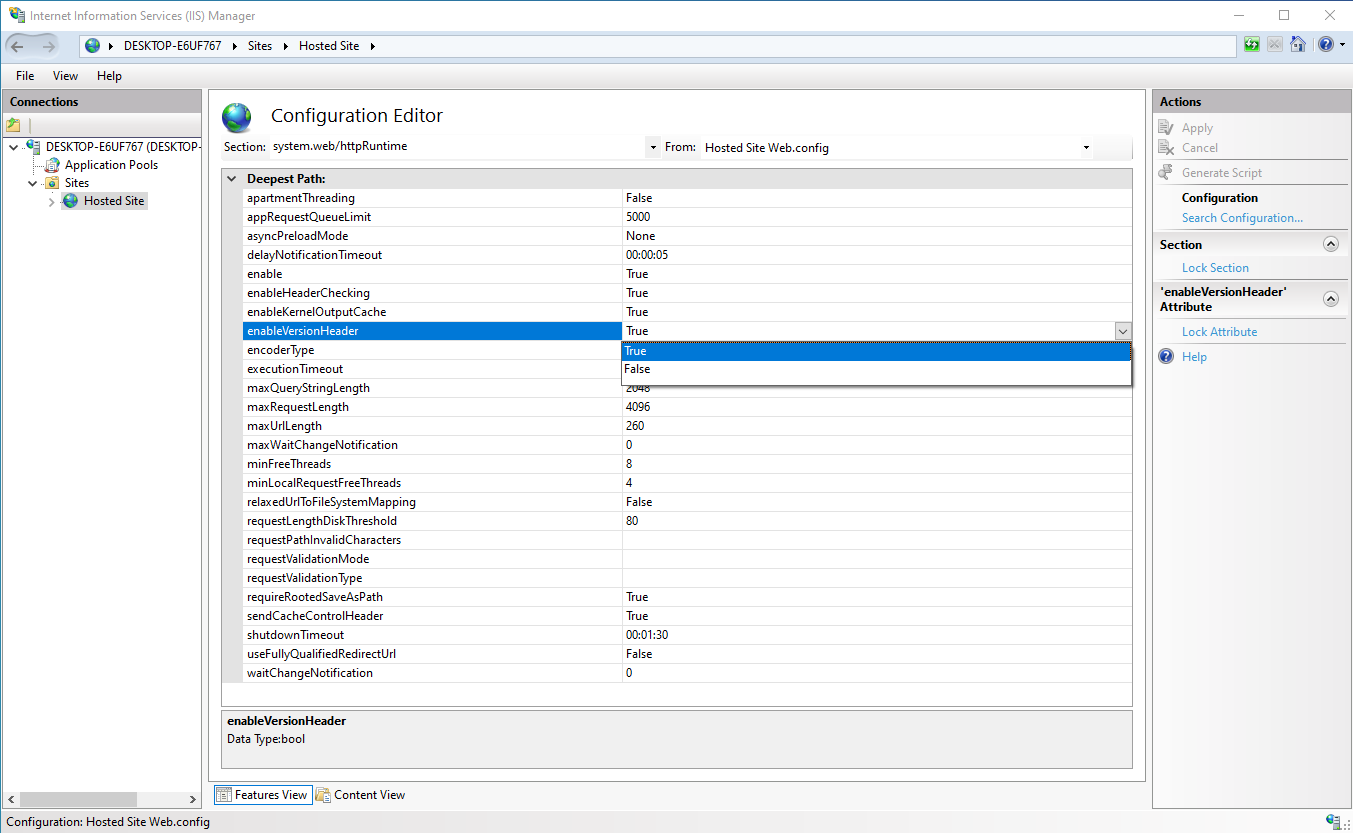
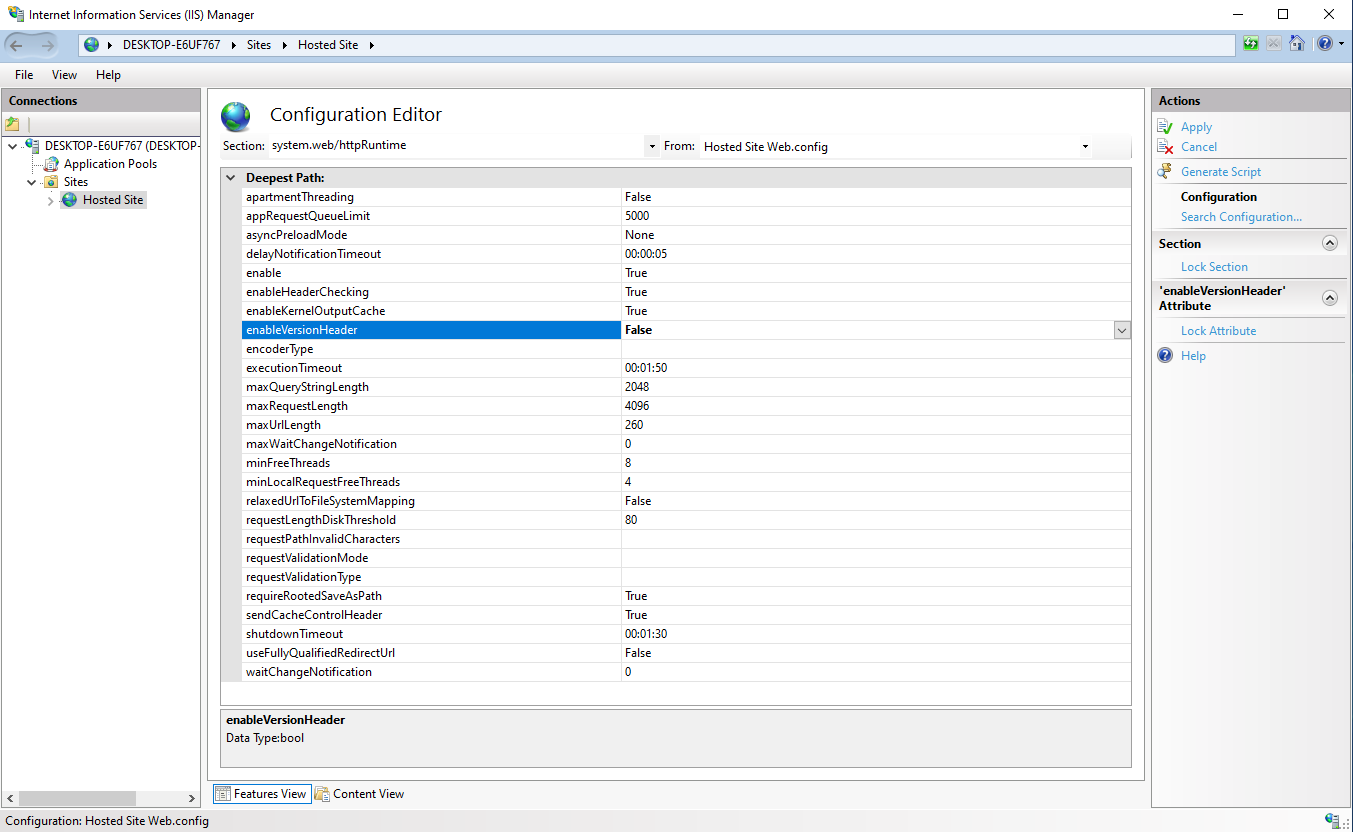
After the variable has been updated the changes will have to be saved, and to do so there is the Apply button in the top right corner.
Once the changes have been applied, the message "The changes have been successfully saved." shows up.
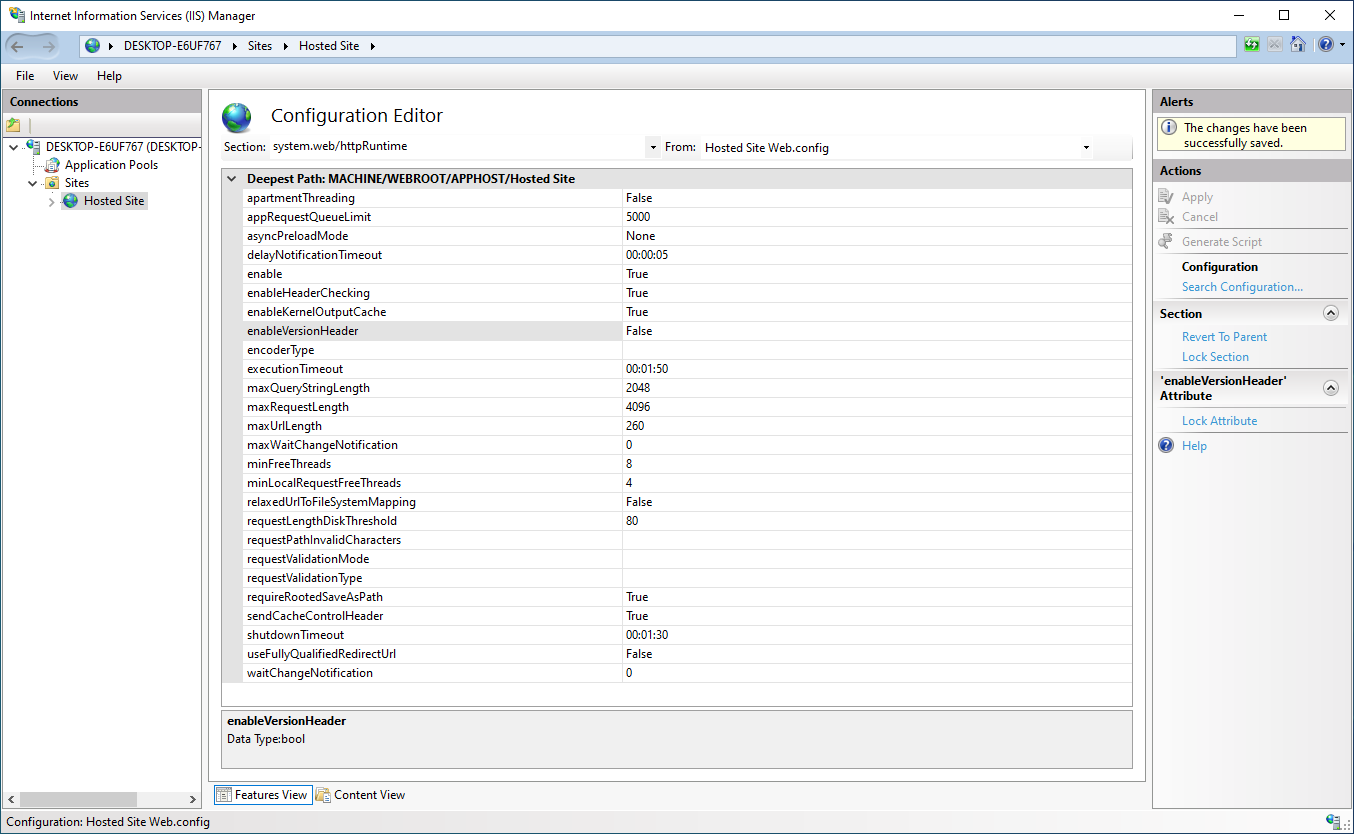
Now to remove the Server header use the same Section menu as before and go to:system.webServer > security > requestFiltering
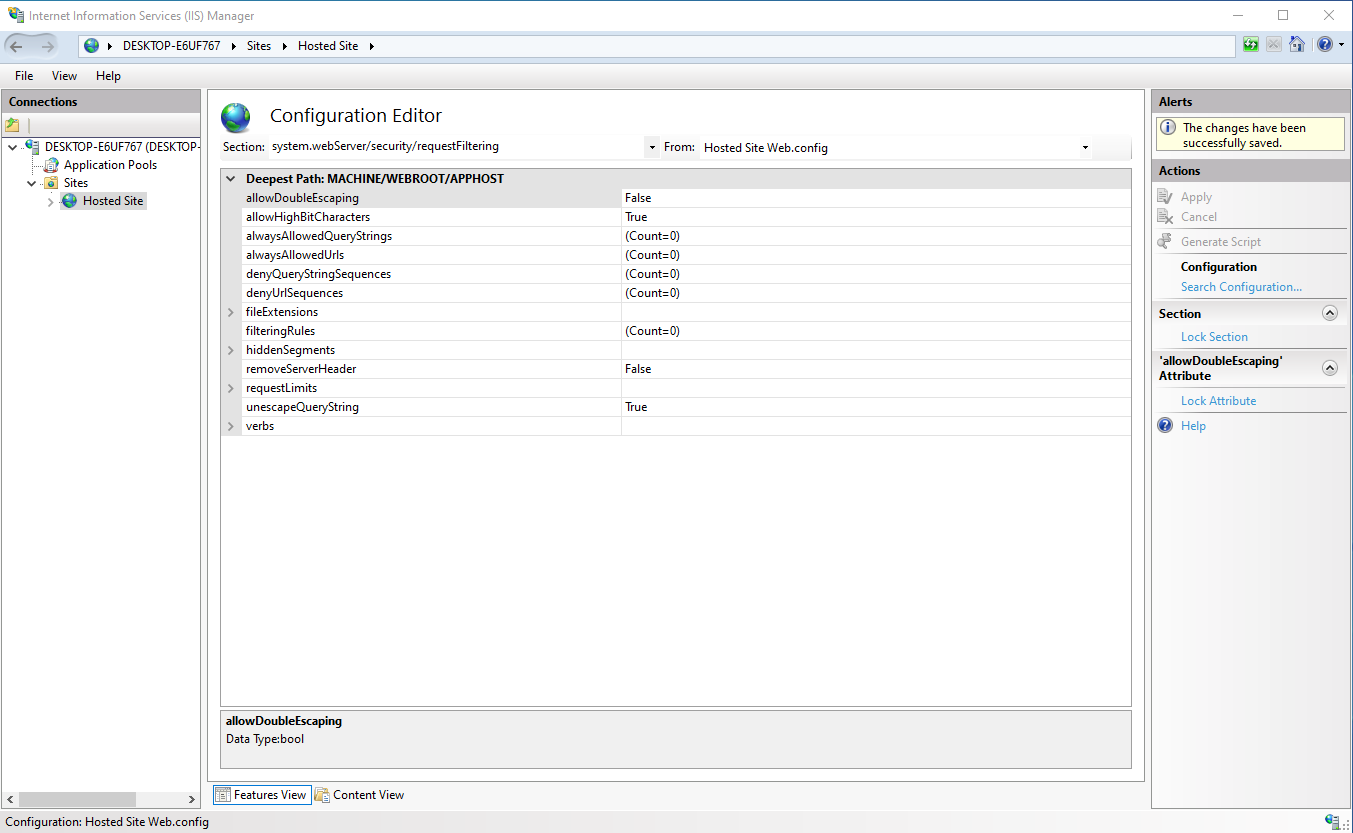
In the same fashion, update the removeServerHeader variable to True.
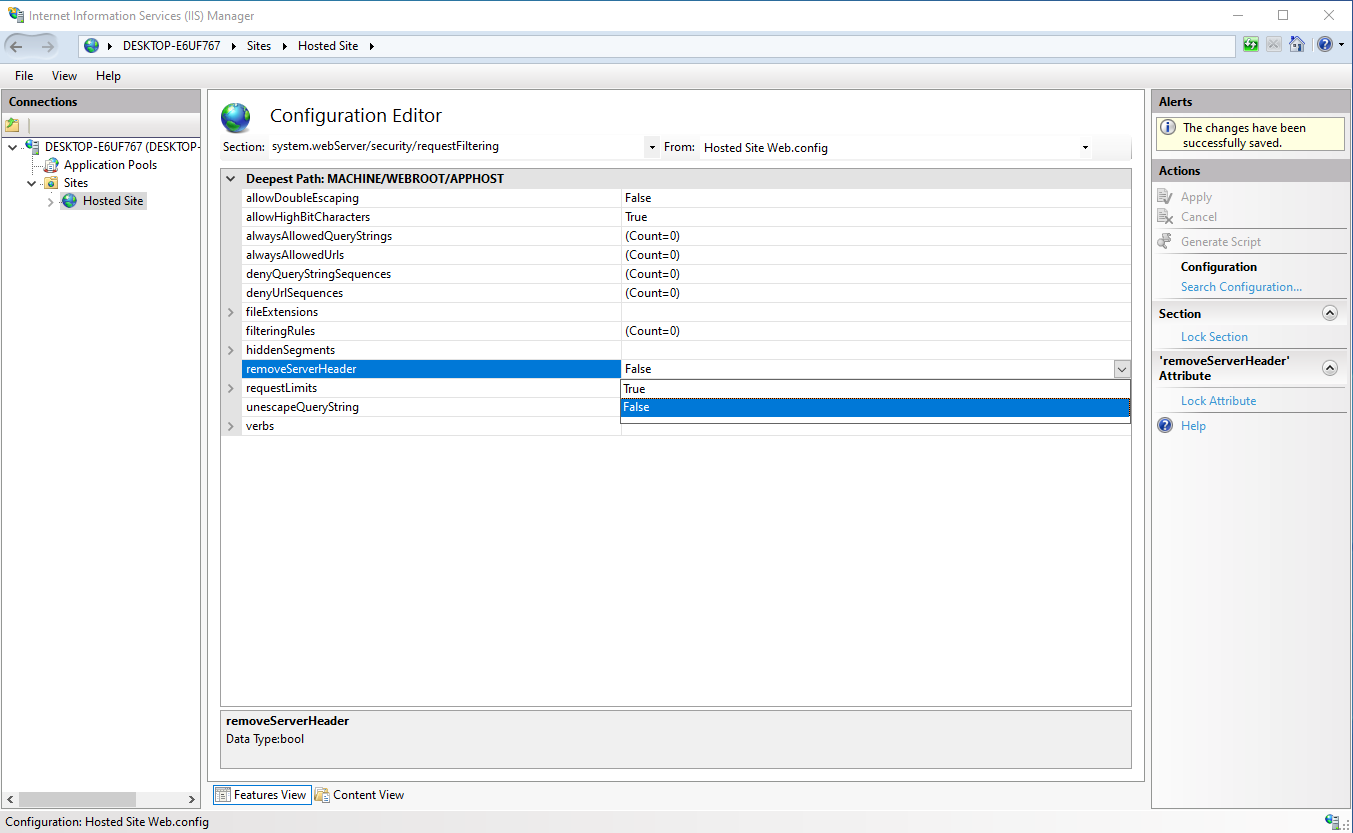
Save the changes like before and now the IIS webserver doesn't respond with any unneeded server information.