Removing the Nuisance of TLS Vulnerabilities from Your Vulnerability Scans
It's common for organisations to have a penetration test report or vulnerability scan done and see infrastructure vulnerabilities of outdated SSL or TLS version and cipher suites in use.
Looking at the CVSS of some of these issues you'd think that you're on the brink of being hacked if you don't remediate them.
In reality, you're likely fine.
They are generally seen as a nuisance on both sides of the field, to fix and to report on.
It's much more of a security hygiene exercise.
Titles like:
- SSL Version 2 and 3 Protocol Detection - Critical
- SSL Medium Strength Cipher Suites Supported (SWEET32) - High
- TLS Version 1.1 Deprecated Protocol - Medium
- TLS Version 1.0 Protocol Detection - Medium
- SSL RC4 Cipher Suites Supported (Bar Mitzvah) - Medium
All seem to thrive in vulnerability reports and are relatively simple to fix.
We'll take a look at a few commonly used webservers for Windows and Linux.
Windows IIS
Running a quick scan for allowed protocols against our IIS server shows that TLSv1.0 and v1.1 are enabled.
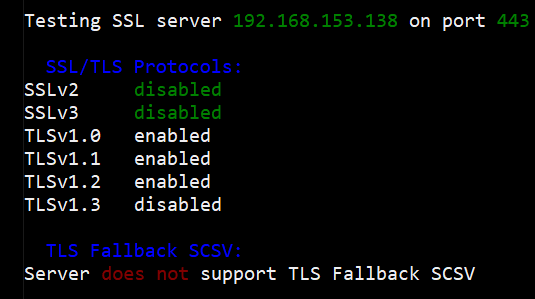
To remove the old versions of TLS from the list, we're going to add in a couple of registry keys to prevent the server from using the default options.
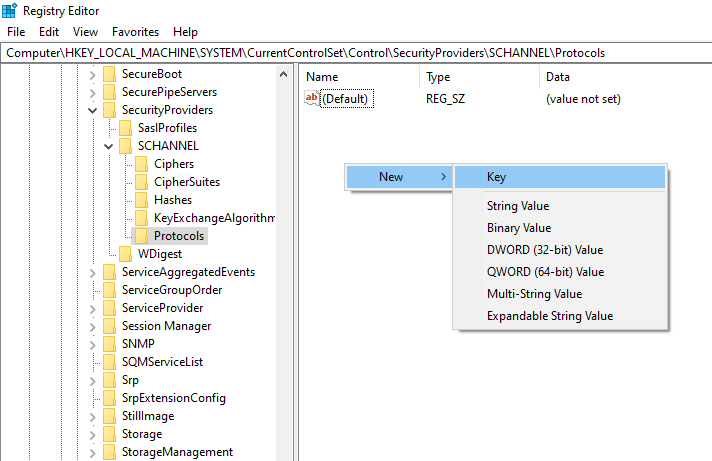
Open the registry editor and find the path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
It will be blank be default so you'll have to create the keys for each version initially.
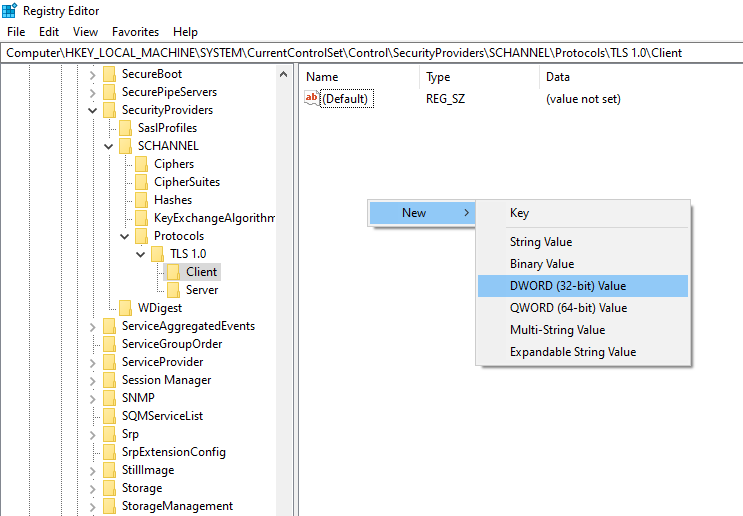
Create a Key value TLS 1.0.
Within the new TLS 1.0 key, add another Key for both Client and Server.
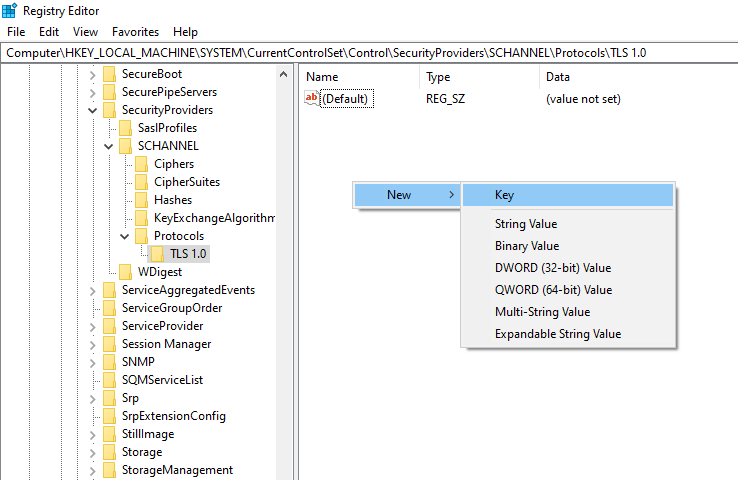
Inside each of the Client and Server keys is where the actual configuration will sit.
To do so, create DWORD values Enabled and DisabledByDefault.
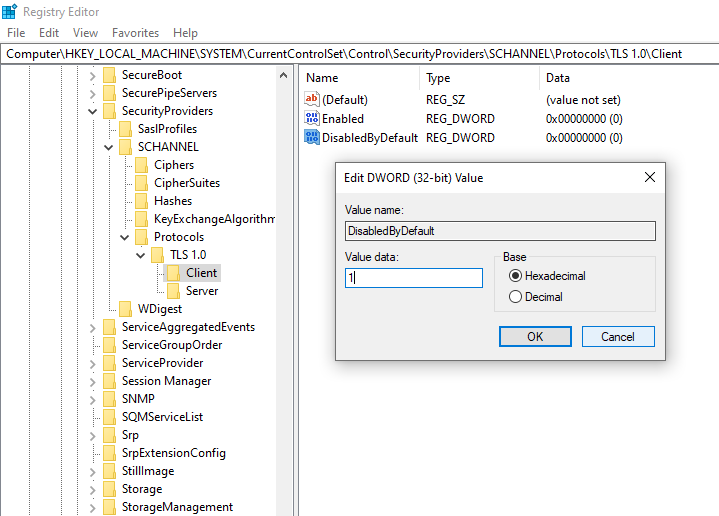
When you create the Enabled value it will be 0 and can be left alone.
For the DisabledByDefault value, update the value to 1 by double clicking the name of the value.
Afterwards, just replicate the structure and value for TLS 1.1 and you should have something like.
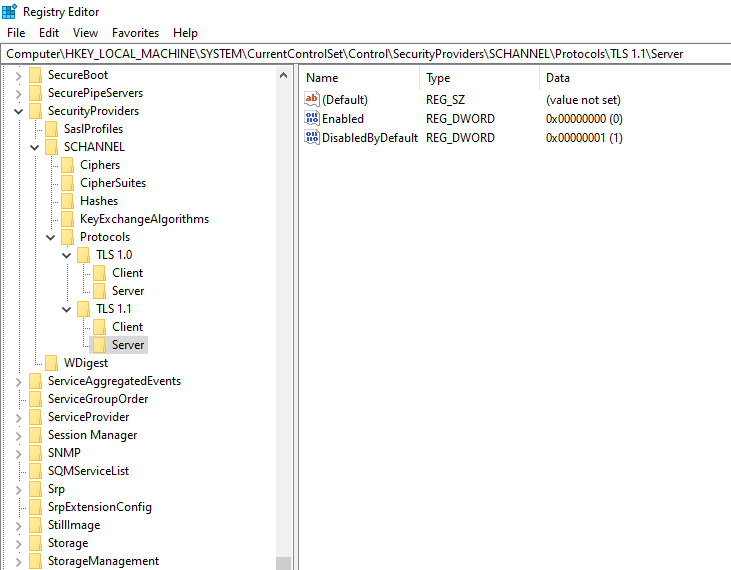
Since the changed registry keys are read at system startup, the webserver needs to be rebooted.
Once complete, the initial scan can be rerun and the old versions of TLS are no longer available.
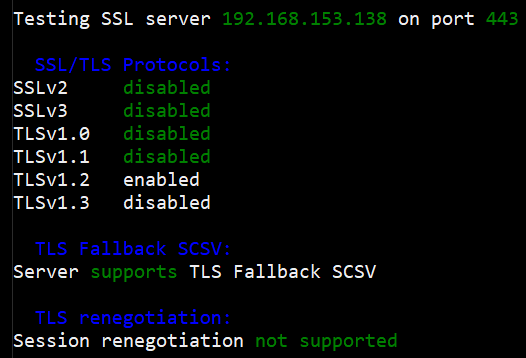
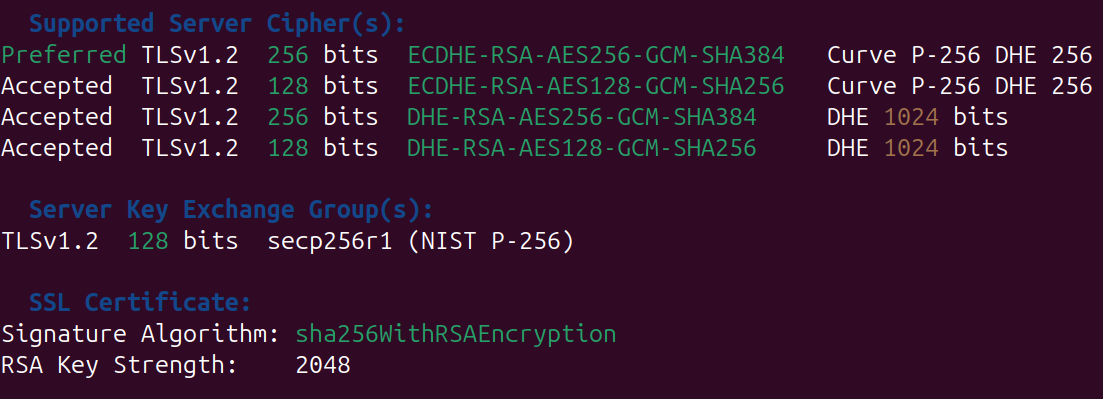
Now to look at the cipher suites, if we took the results from the initial scan, it shows that weak ciphers are used, in your vulnerability report, there may be cipher suites with less than 112 bits or using encryption such as 3DES or RC4.
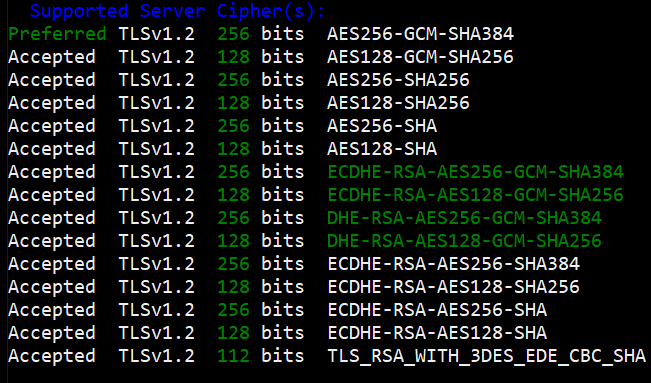
To remove the weak cipher, we'll use a GPO to specify which cipher suites we want to use on our webserver.
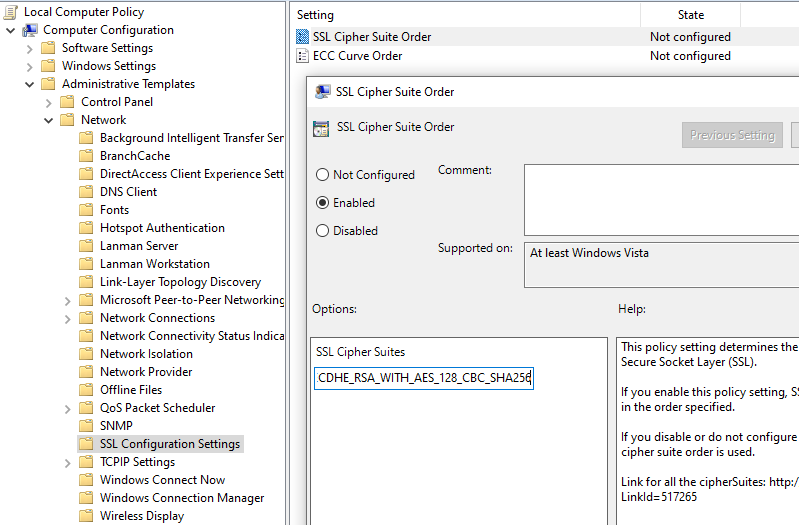
Inside the group policy editor, find the setting SSL Cipher Suite Order at:
Computer Configuration > Administrative Templates > Network > SSL Configuration Settings > SSL Cipher Suite Order
Enable the setting and specify the SSL Cipher Suites value as:
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
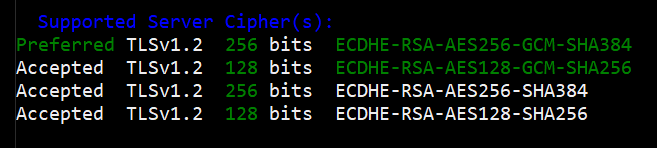
After the group policy is applied, and the server is rebooted, the updated cipher suites can be seen.
Linux Apache
The same scan run on a default Apache webserver results in the same TLS v1.0 and v1.1 showing up.
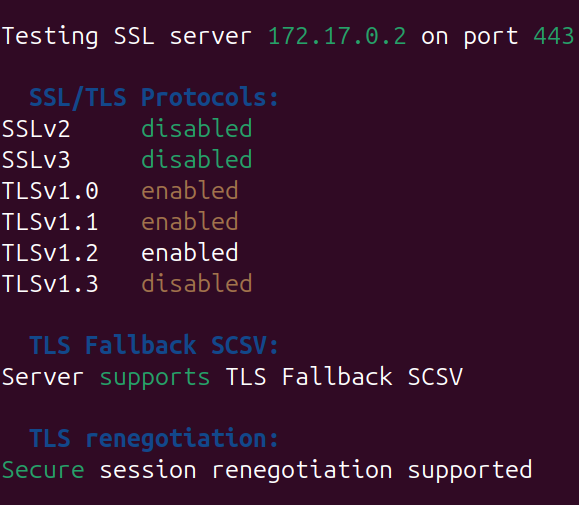
Looking at the configuration file for the TLS settings shows that only SSLv3 is blocked as an option.
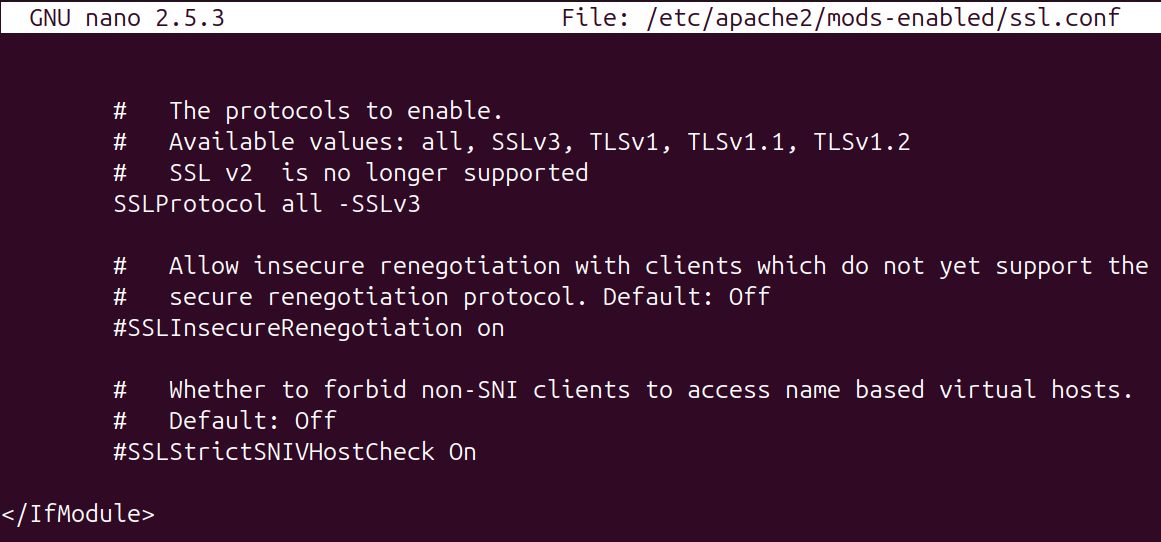
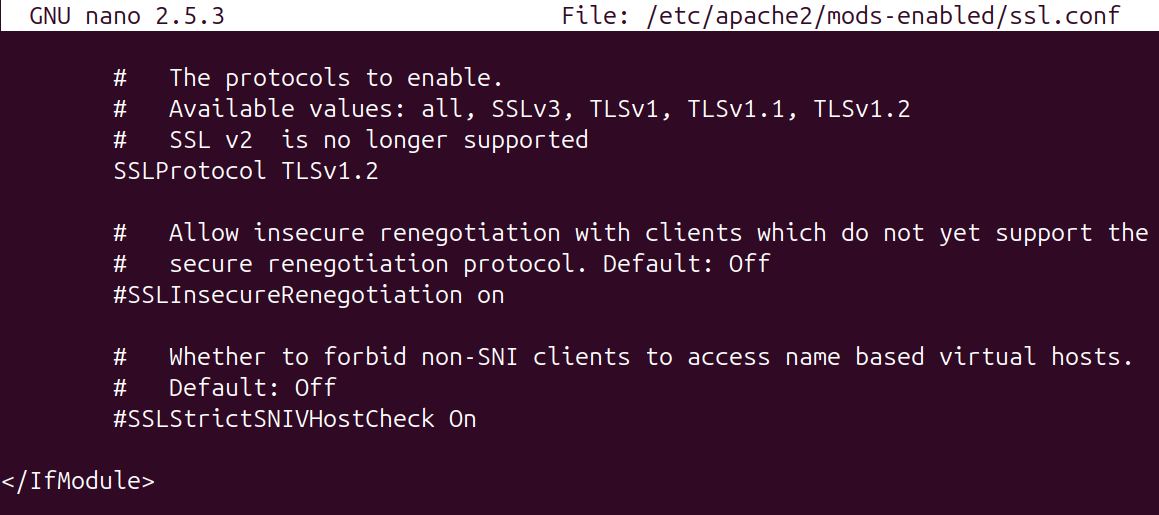
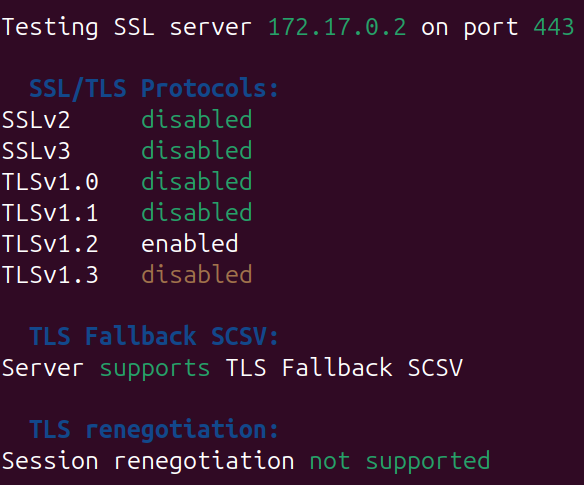
To remove the unsafe protocols TLS v1.2 can be explicitly set.
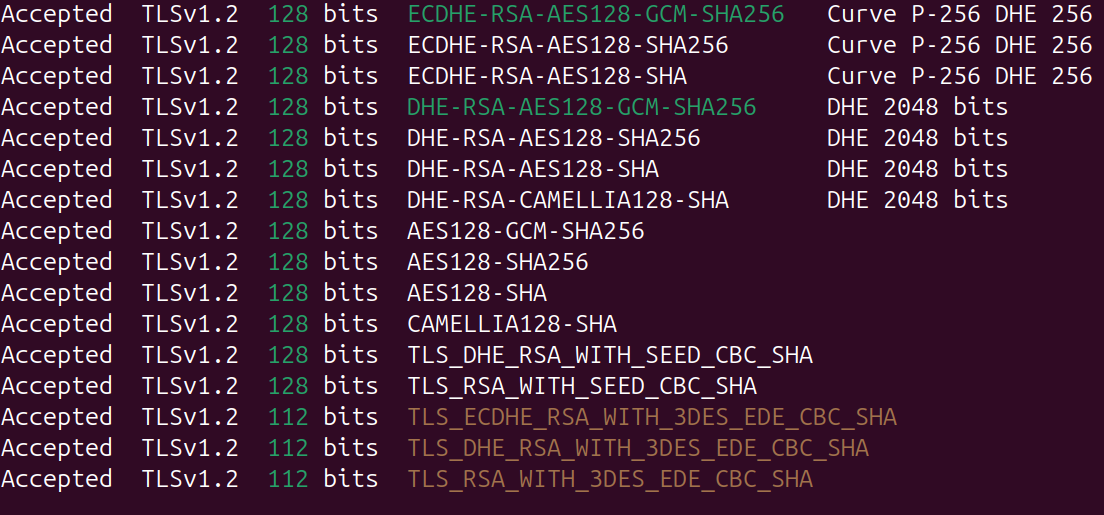
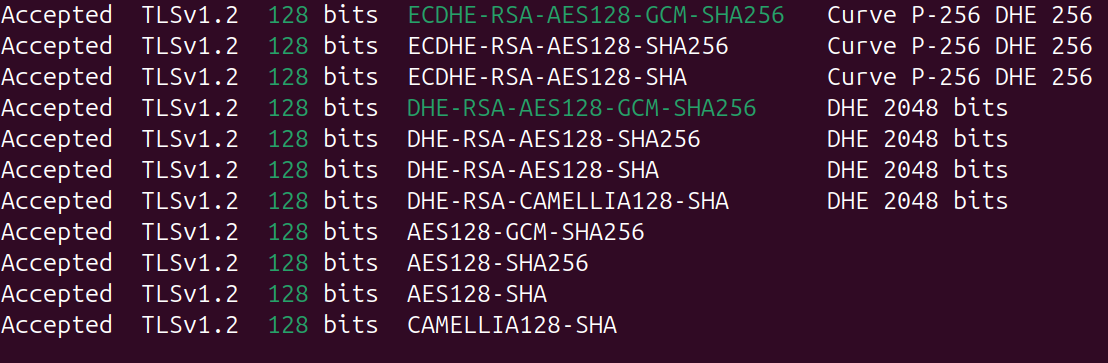
Now taking a look at the default ciphers, there are a couple that are highlighted in yellow which are regarded as weak.
The configuration file /etc/apache2/mods-enabled/ssl.conf shows that all ciphers are initially allowed and a denylist is used to remove unsafe ciphers.
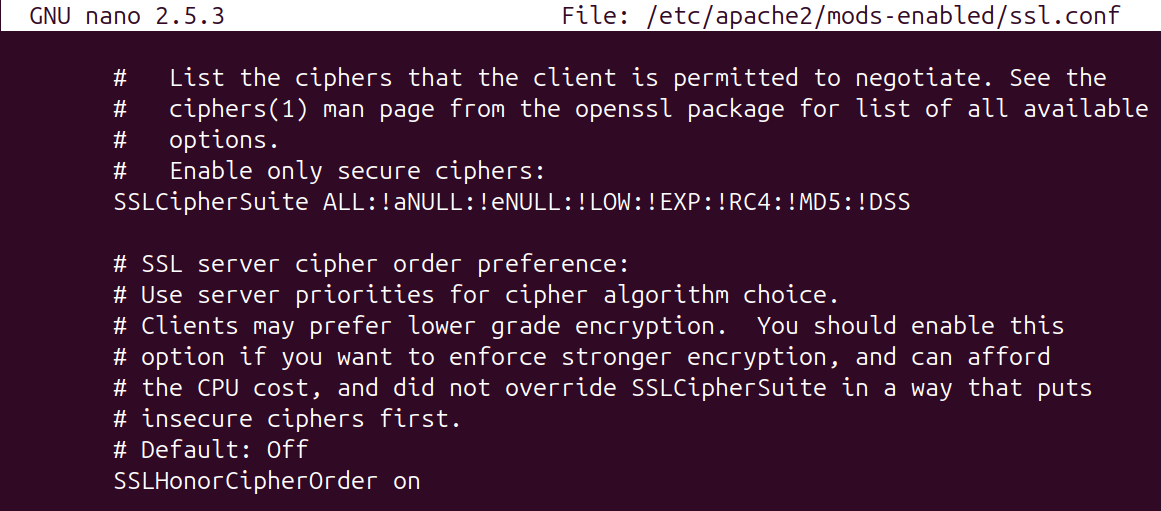
There is another approach which is to allowlist the secure ciphers and block unsafe ciphers by default.
With the allowlisting updates to the SSLCipherSuite variable.
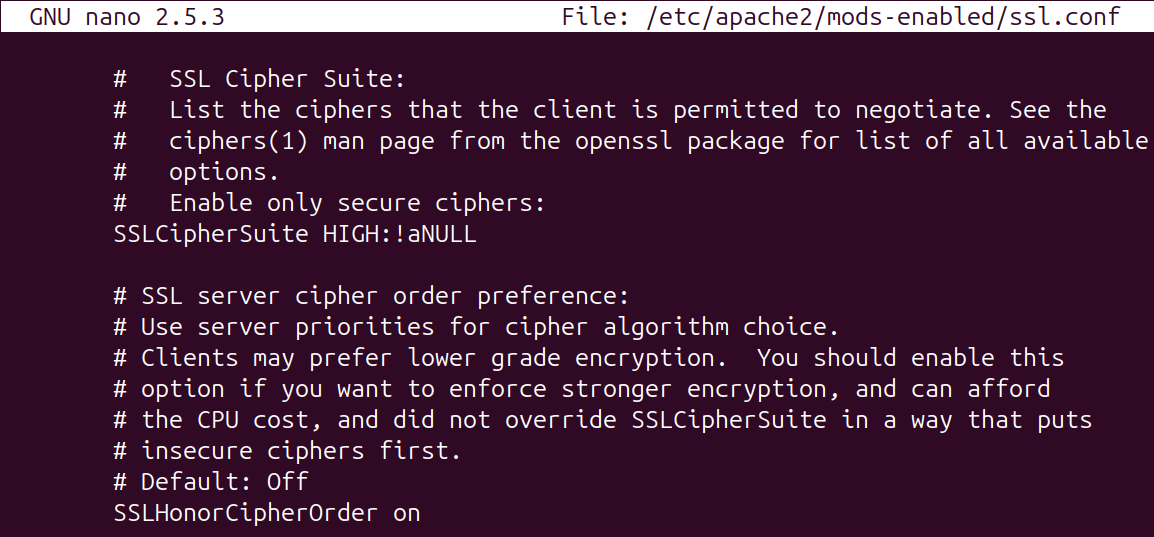
That will tell Apache to use only strong encryption ciphers and exclude any cipher that has no authentication.
Now that the Apache config is all set, restart the Apache service and you should see results like.
Linux Nginx
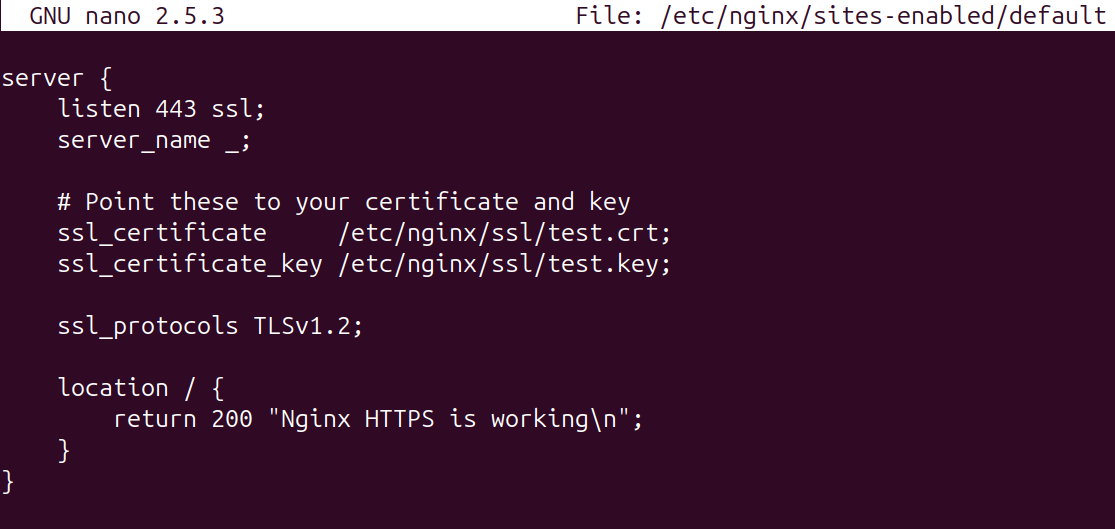
To resolve the weak TLS and cipher suites used in the Nginx site, the configuration file can be updated to explicitly allow safe and modern protocols.
As an example, a default Nginx site has been spun up and the SSL configuration contains SSLv3, TLSv1.0 and TLSv1.1.
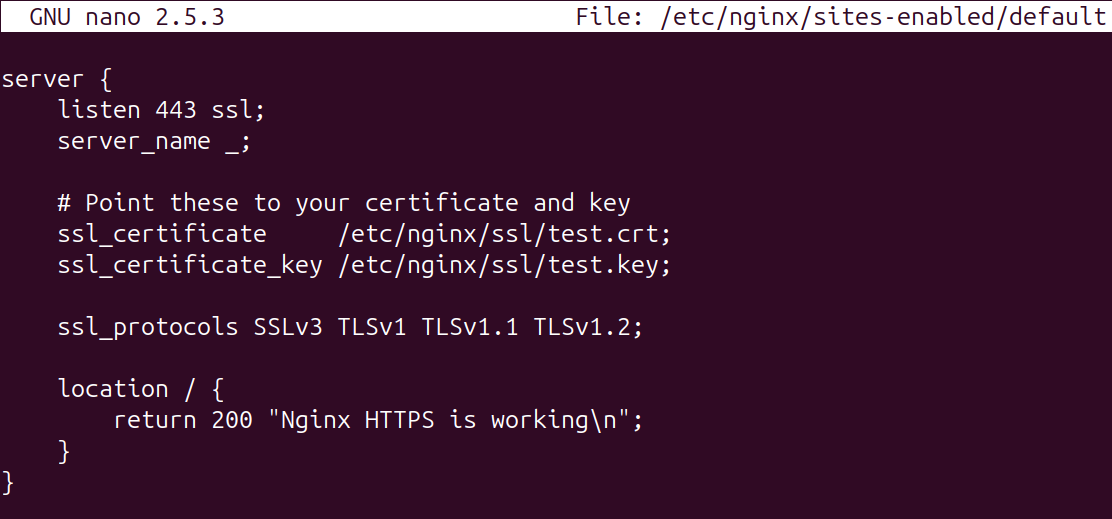
The solution is straightforward, and the only update is to remove the old protocols from the list, which will look like.
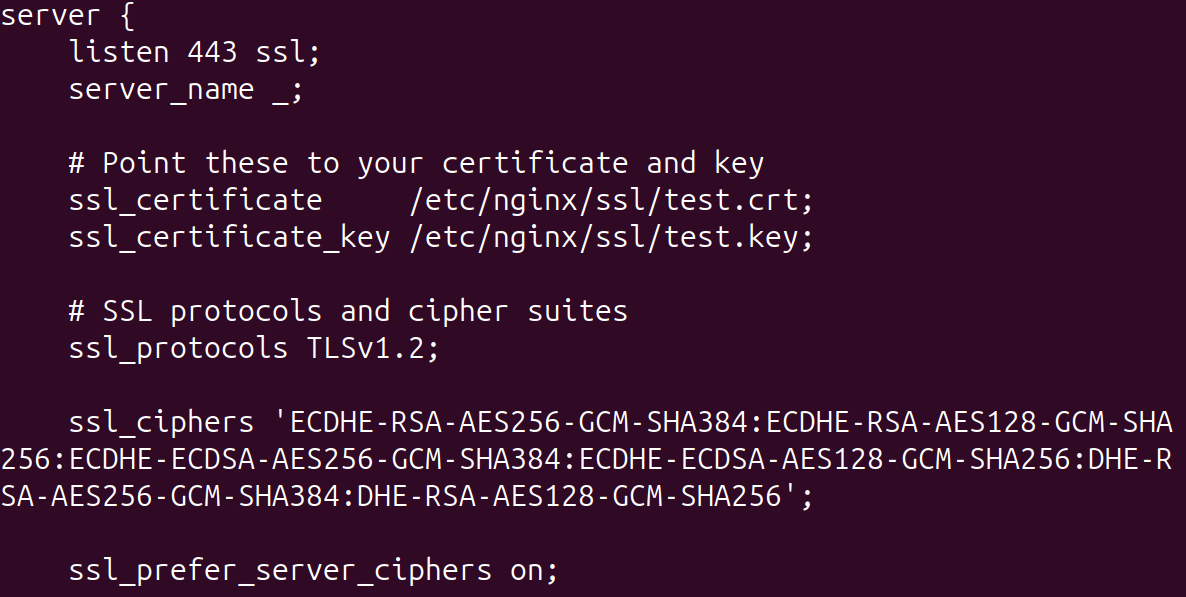
To solve for the weak cipher suites, they will need to be listed in the file.
We've chosen a group of safe and modern ciphers compatible with TLS 1.2.
ssl_ciphers 'ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256';
With the configuration updated, a quick Nginx restart will show the new list of cipher suites.